KrakenD Enterprise 2.2 released
by Albert Lombarte
The new KrakenD Enterprise version 2.2 is now available, and it’s supercharged: Introduces dynamic routing based on headers and query strings, adds a security policies engine, upgrades to OpenAPI 3, improves SOAP integration, default gzip compression and a lot more…
Below there is a summary of changes and an introduction to some of these new features.
Security Policies: Enforce any check, anywhere
From RBAC and ABAC, to lifecycle management, restriction of content by country, validation custom cryptography or other strategies, … The new policies engine allows you to do any custom evaluations you need, during runtime and with access to query strings, URLs, parameters, cookies, tokens, time functions, geolocation, cryptography, and a long etcetera.
Here’s a couple of elementary examples:
// Is the user from the right department?
has(JWT.department) && JWT.department in ["marketing", "sales"]
Or
{
"req": {
"policies": [
"timestamp(now)< timestamp('2023-01-01T10:00:20.000-05:00') || timestamp(now)> timestamp('2023-01-01T12:00:20.000-05:00')"
],
"error": {
"body": "The system is down for maintenance from 10am to 12pm. Come back later",
"status": 500
}
}
}
Policies are potent and allow you to perform many checks and return custom errors before or after hitting your services, see some examples.
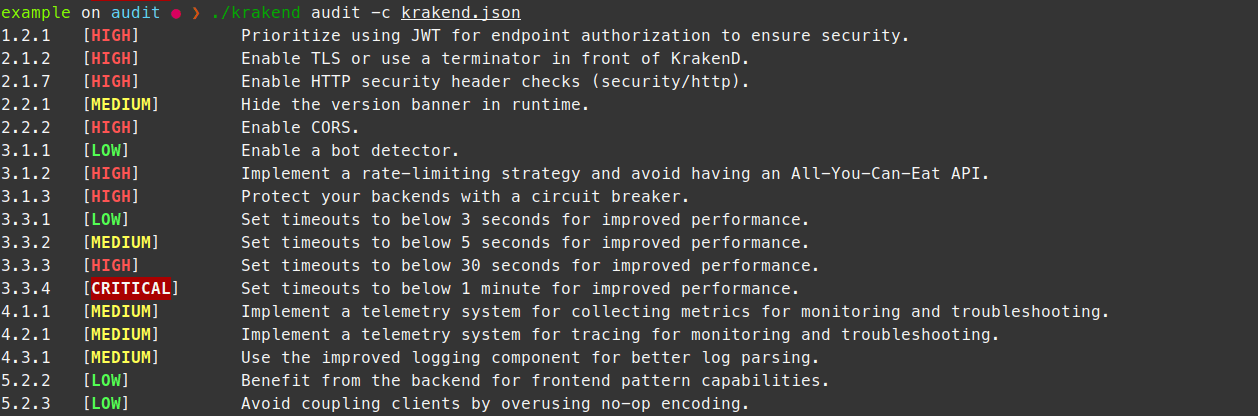
Security Audit: Automated advice on your pipeline
The security audit command (krakend audit) parses and analyzes your configurations and outputs security recommendations. We have designed it to run as a standalone command or integrated it into your existing CI/CD pipeline to avoid dangerous configurations, such as unwillingly disabling the TLS, setting excessive timeouts, unprotected endpoints, or similar scenarios.
Dynamic routing based on headers and query strings
The dynamic routing extends the routing capabilities to add header and query string processing to assemble the final upstream URL you want to reach.
{
"endpoint": "/foo",
"backend":[
{
"url_pattern": "/{input_headers.X-Tenant}/foo"
}
]
}
JWT validation
Improvements on the JWT validator:
- Extraction of JSON from paths in JWT claims has been improved
- JWT is now more restrictive and fallbacks to returning 401 error codes with incorrect configurations.
- The JWK URL requests to your identity server now include a KrakenD-specific user agent.
New manipulation options
In this category, we have enabled the following features:
- The SOAP integration with data injection allows you to expose GET endpoints that send dynamic POST data generated with templates
- The JMESpath Query Language is now available on backends, extending the endpoint-level functionality
- Body transformation and generation. Create the body of requests using templates and inject other input data like headers, query strings, or URL parameters.
Connectivity
- Header and Query string routing a much claimed functionality!
- Gzip compression to all outgoing traffic by default.
- SOAP integration with data injection using templates
- HTTP proxy plugin, to connect to all or some backends using a corporate proxy.
- Jaeger exporter now supports the UDP protocol to post traces to a Jaeger-agent.
- Bot Detector adds the flag
empty_user_agent_is_botto define empty user agent treatment.
OpenAPI 3
Added OpenAPI 3 through flag --oas3 supporting import, export, mocking, and JSON schema. The previous Swagger 2.0 has received improvements as well.
Configuration
- Flexible Configuration component upgrades Sprig from v2 to v3. This has changes in the way
^is handled. Some new functions available arefromJson,addf,maxf,mulf,osBase,osDir,osExt,osClean, orosIsAbs. - Flexible Configuration with YAML or TOML is now possible.
🚀 Summary of changes for EEv2.2
The v2.2. introduces a new security policies engine, routing based on headers, OpenAPI 3, SOAP integration with custom body generation, everything on Community 2.2.1, and more.
- New Dynamic Routing based on headers and query strings.
- New Security Policies engine.
-
New
krakend auditcommand. - JMESpath Query Language at the endpoint level
- New SOAP integration with data injection
- New Body manipulation and generation
- New HTTP proxy plugin
- Support for OpenAPI 3
- UDP on Jaeger exporter.
- The Bot Detector adds the flag empty_user_agent_is_bot to define empty user agent treatment.
- Output adds gzip compression
- Flexible Configuration upgraded
- Improvements on the JWT validator
- Upgraded Basic Authentication
- When you were loading multiple plugins, and one of them failed, the gateway did not load the rest. Now the sequence will continue excluding the failing one.
- Older Docker images raised false positives when performing security scans due to an unused but included library (Thrift server). This library is no longer in the code.
Upgrading to the latest version is always advised.