KrakenD 2.2 Release Notes: Latest Features and Enhancements
by Albert Lombarte
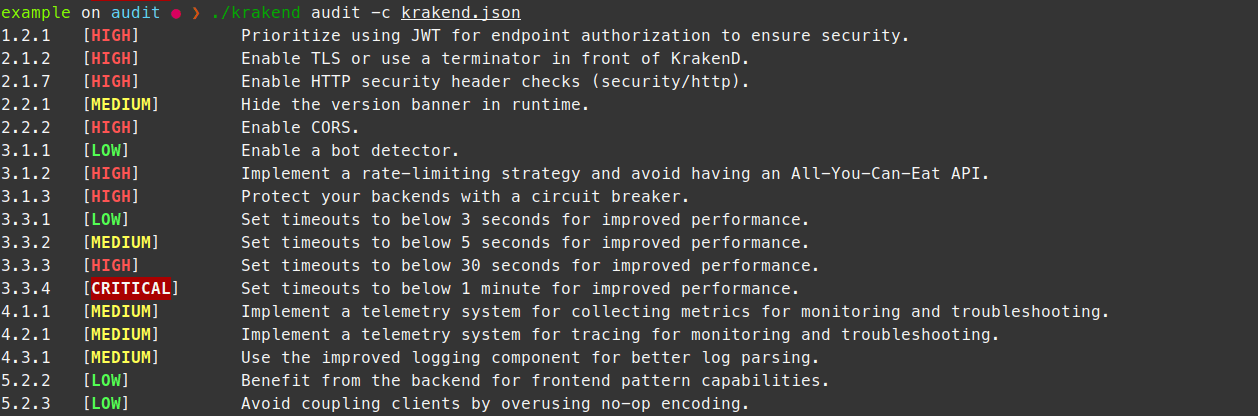
The KrakenD team is pleased to announce the release of KrakenD Community Edition v2.2. It introduces a new security audit command (krakend audit) that parses and analyzes your configurations and outputs security recommendations. We have designed it to run as a standalone command or integrated it into your existing CI/CD pipeline to avoid dangerous configurations, such as unwillingly disabling the TLS, setting excessive timeouts, unprotected endpoints, or similar scenarios.
You can get v2.2 packaged for several options from the download page.
🚀 Summary of changes for CEv2.2
It introduces a new security audit command (krakend audit) that parses and analyzes your configurations and outputs security recommendations. We have designed it to run as a standalone command or integrated it into your existing CI/CD pipeline to avoid dangerous configurations, such as unwillingly disabling the TLS, setting excessive timeouts, unprotected endpoints, or similar scenarios.
- When you were loading multiple plugins, and one of them failed, the gateway did not load the rest. Now the sequence will continue excluding the failing one.
- Older Docker images raised false positives when performing security scans due to an unused but included library (Thrift server). This library is no longer in the code.
-
The
krakend auditcommand. -
The Flexible Configuration component upgrades Sprig from v2 to v3. This has changes in the way
^is handled. Some of the new functions available arefromJson,addf,maxf,mulf,osBase,osDir,osExt,osClean, orosIsAbs. It also documents how to useyamlortomlto write configurations using FC. - The Jaeger exporter now supports the UDP protocol to post traces to a Jaeger-agent.
-
The Bot Detector adds the flag
empty_user_agent_is_botto define empty user agent treatment. - JWT: Extraction of JSON from paths in JWT claims has been improved
- JWT is now more restrictive, and fallbacks to returning 401 error codes with incorrect configurations.
- The JWK URL requests to your identity server include now a KrakenD-specific user agent.
Upgrading to the latest version is always advised.
Commit changelog
List of all changes in KrakenD Community Edition and its krakend packages in use between v2.1.4 and v2.2.0
Commits in KrakenD-CE
- v2.2.0 bumped
- botdetector pkg updated
- flexibleconfig pkg updated
- opencensus pkg updated
- ratelimit pkg updated
- deps updated
- cobra pkg upgraded
- usage pkg upgraded to v2
- audit cmd added
- Add git to the alpine builder to be able to install modules without GOPROXY.
- Add security scanning to container images
- Use the recommended replacements for
io/ioutilfunctions - Add security scan for the repository
Changes in krakend-audit
- give better recommendation messages
- audit package to check security recommendations
- Initial commit
Changes in krakend-botdetector
- Autofix issues in 1 file
- flag to reject requests with empty user-agent added
Changes in krakend-cobra
- Autofix issues in 1 file
- audit pkg updated
- remove colors if not running on a tty
- write the recommendations on stderr
- update deps
- minor refactor
- Change terminal colors
- add colors to severity levels if executed in a terminal
- audit pkg updated
- return status 1 when there are recommendations
- minor refactor
- minor refactor
- audit command added
Changes in krakend-flexibleconfig
- avoid using deprecated function
- avoid using deprecated function
- use DirEntry instead of FileInfo
- Autofix issues in 2 files
- sprig upgraded to v3
- gh workflows upgraded
Changes in krakend-jose
- gh workflow updated
- Autofix issues in 2 files
- double check the handler is never executed when parsing fails
- return a 401 handler if config parser fails
- upgrade go version
- reuse the claim extractor
- gocloud version upgraded to v0.28.0
- send a custom user agent when requesting the JWK
- improve json extraction
Changes in krakend-opencensus
- Unused parameter should be replaced by underscore
- jaeger exporter updated
Changes in krakend-ratelimit
- fix ClientCapacity does not have correct default value when MaxRate is zero